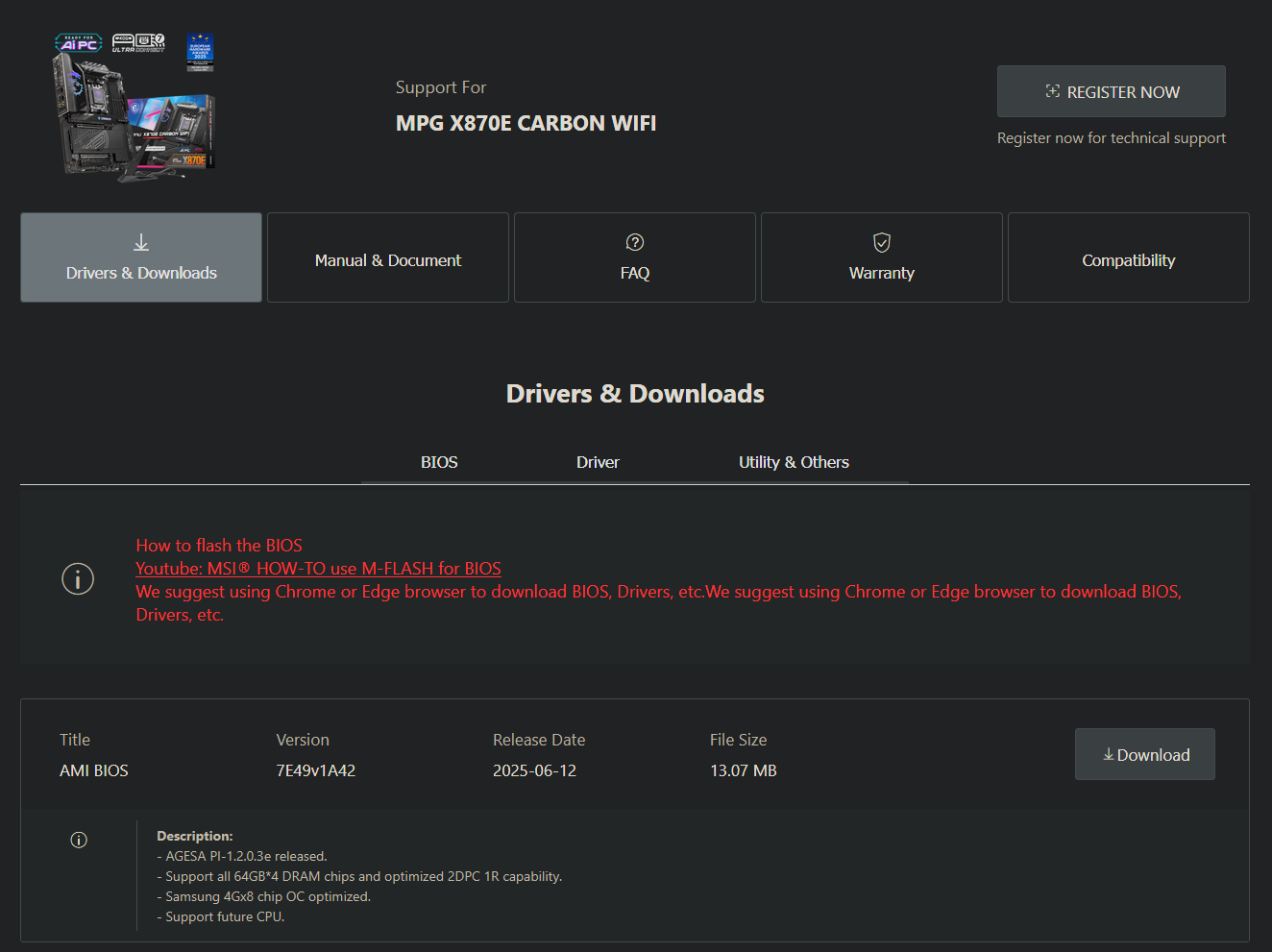
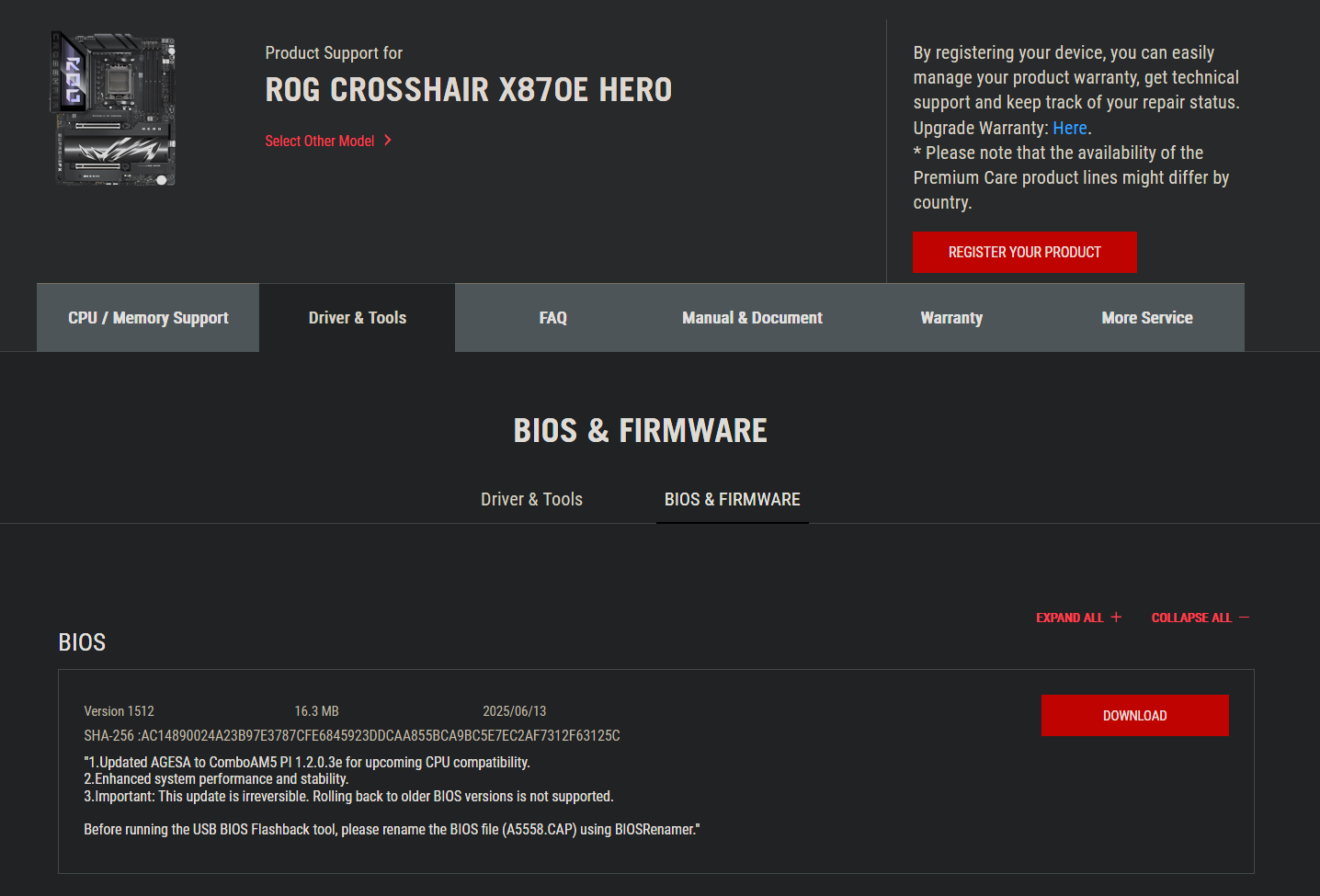
Board partners are now rolling out freshly baked BIOS updates based on AMD’s AGESA 1.2.0.3e firmware. The updates are designed to patch a security flaw that could allow hackers to read sensitive data stored within the TPM (Trusted Platform Module), via VideoCardz. At least for some manufacturers, this BIOS update is a one-way street; you cannot roll back to an older release once you install it.
Hackers can exploit this security flaw by triggering an out-of-bounds read beyond the TPM2.0 routine. By doing so, these unauthorized users can gain access to sensitive data or disrupt the TPM’s functionality as a whole. This stems from a bug (CVE-2025-2884), ranked 6.6 (Medium) on the CVSS scale, in TPM2.0’s Module Library, which refers to standardized code that TPM 2.0 chips use for various functions.
While the AGESA 1.2.0.3e firmware only targets AM5-based processors, the security bug it addresses impacts a much wider range of AMD CPUs. Hence, it’s best to consult the official security bulletin to determine if a mitigation is available for your processor. What makes this particular bug concerning is its accessibility, since it can be exploited using standard user-mode privileges, meaning an attacker doesn’t need kernel-level access. This is a significant difference from previous vulnerabilities, including one that could execute unsigned microcode but required kernel-level access.
Impacted processors include a wide range of Ryzen processors between Athlon 3000 “Dali” / Ryzen 3000 “Matisse” and Ryzen 9000 “Granite Ridge” on desktop, and between Ryzen 3000 Mobile “Picasso”, and Ryzen AI 300 “Strix Point” on mobile. Similarly, all workstation CPUs from Threadripper 3000 “Castle Peak” to Threadripper 7000 “Storm Peak” are also vulnerable to this bug. That being said, patches for most of these processors have been deployed across different timelines in the past few months. AM5-based CPUs are the most recent and are the latest to receive the update.
Several motherboard partners, including Asus and MSI, have started to roll out BIOS updates based on the new AGESA 1.2.0.3e firmware. In addition to fixing the aforementioned TPM flaw, this firmware also adds support for a new and upcoming Ryzen CPU, likely alluding to Ryzen 9000F series processors. It is best to consult your motherboard vendor’s support page to see if a new BIOS is available, and update accordingly.
Follow Tom’s Hardware on Google News to get our up-to-date news, analysis, and reviews in your feeds. Make sure to click the Follow button.